After attending VMware EMPOWER earlier this year, I won a voucher for a free exam (thanks EMPOWER team!). I chose the NSX-T 3.1 Data Center Security exam because of personal interest and exciting security features NSX offers. While preparing for the exam I gathered a list of study materials I wanted to share with you all.
The voucher expired on the 31st of August, but got it in mid-July during my PTO. So, work to do 😄. With the voucher at hand, I booked the NSX-T 3.1 Data Center Security exam (5V0-41.21) and passed it! Passing the exam unlocks its skill badge.

Looking at the image below, it sums up the wide range of security features quite well and gives a good overview what the exam covers. Let’s check out the details.
Exam details
As far as I know, this is the first release of a NSX exam dedicated to security. Passing the exam, unfortunately does not count towards the VCP-SEC professional level certification, although both the VCP-SEC and NSX Security exams share similarities.
The actual exam consists of 70 questions which need to be answered in 130 min. and has a passing score of 300 out of 500 points. Non-native English speakers are not given extra time. From my experience the given time was adequate to answer the questions and thoroughly review the marked ones.
Exam preparations
Before taking the exam, VMware recommends to attend the NSX-T 3.0 ICM or NSX-T 3.1 Intrinsic Security course. I did not attend one of the and cannot comment on that. About the experience part, I think you can go for this exam if you have a good (vSphere and NSX-T) networking knowledge and functional knowledge of security related products. When being new to NSX-T, I would recommend to take the 5-day NSX 3.0 ICM training.
The exam guide itself states that the minimally qualified candidate (MQC) should have 1 years experience working in IT and should have hands-on experience with NSX-T and basic knowledge of KVM and vSphere.
Exam sections
A VMware exam guide is standardized to seven sections nowadays. According to the guide, this exam test on 4 of them. The MQC should have sufficient knowledge contained in the exam sections below. The exam guide does a good job providing a list of objectives to be tested against.
- Section 1 – Architecture and Technologies
- Section 2 – Products and Solutions
- Section 3 – Planning and Designing
- Not tested on this objective
- Section 4 – Installing, Configuring, and Setup
- Section 5 – Performance-tuning, Optimization, and Upgrades
- Not tested on this objective
- Section 6 – Troubleshooting and Repairing
- Section 7 – Administrative and Operational Tasks
- Not tested on this objective
In the upcoming sections you can expect an overview of the materials I used for every on of the objectives in the exam guide. During my study I took notes in OneNote for every of the objectives. The info below is based on that.
Generic readings
NSX-T Security Reference Guide
This one helped me the most. It’s a very well written guide, that covers a lot of objectives in the exam guide.
I found this useful and detailed list of terms just recently and is a good source of information for objectives in this exam.
Section 1 – Architecture and Technologies
Objective 1.1: Describe information management security
What Is Information Security Management and Operations?
Objective 1.2: Describe firewalls and their function
Objective 1.3: Describe IDS/IPS
VMware NSX Distributed IDS/IPS
Objective 1.4 – Describe Zero-Trust Security
Objective 1.5 – Describe AAA and CIA
Confidentiality, Integrity, and Availability (CIA) triad
What is CIA Triad of information Security?
Section 2 – VMware Products and Solutions
Objective 2.1 – Describe VMware Security portfolio
VMware Security portfolio overview
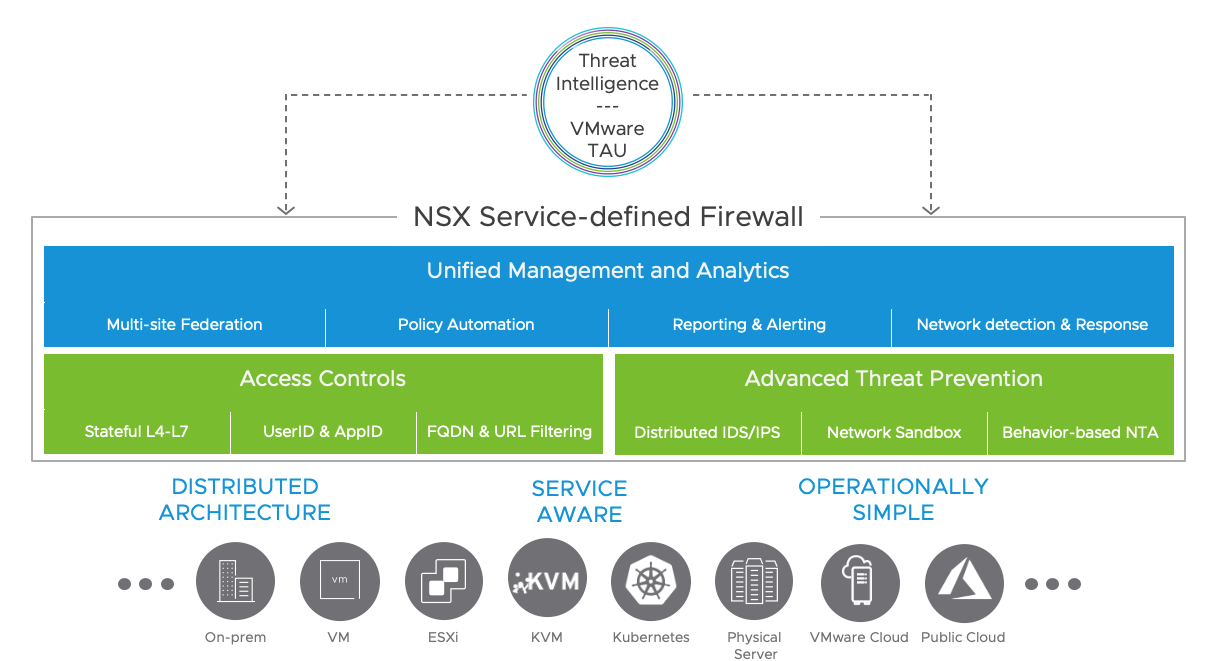
NSX Service-defined Firewall (overview)
NSX Service-defined Firewall (Datasheet PDF)
Objective 2.3 – Describe NSX Distributed Firewall
NSX Data Center (Datasheet PDF)
NSX Security Reference Guide – 4.3 Distributed Firewall
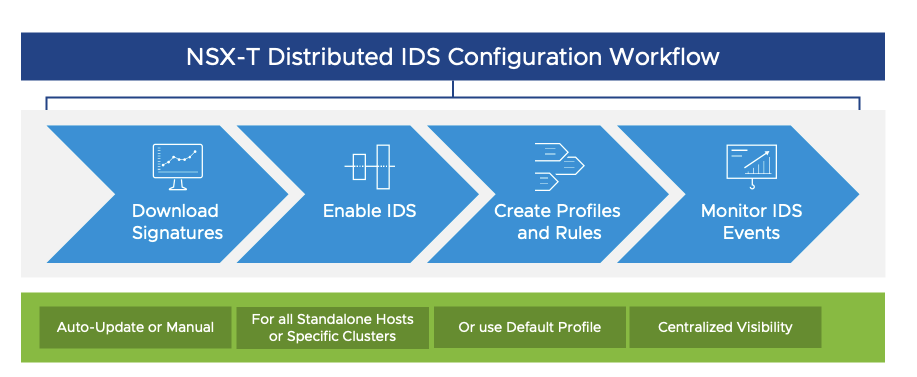
Objective 2.3 – Describe NSX Distributed IDS/IPS
NSX Distributed IDS/IPS (overview)
NSX Distributed IDS/IPS (Solution Overview PDF)
NSX Security Reference Guide – 8 Intrusion Detection and Prevention
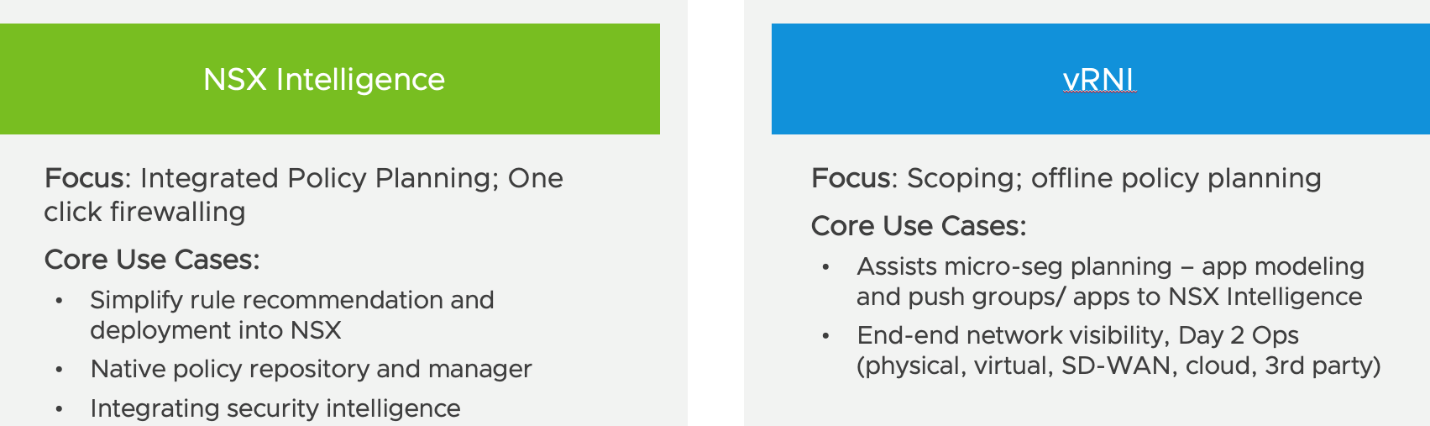
Objective 2.4 – Describe NSX Intelligence
NSX Intelligence (Solution Brief PDF)
NSX Data Center (Datasheet PDF)
Easily Operationalize Micro-segmentation with NSX Intelligence (White Paper PDF)
NSX Security Reference Guide – 10.2 NSX Intelligence
NSX Intelligence versus vRealize Network Insight (vRNI)
Objective 2.5 – Describe NSX Edge Security (Gateway Firewall and URL Analysis)
NSX Security Reference Guide – 4.2 Gateway Firewall
NSX Data Center Documentation – URL Analysis Workflow
NSX Ninja – Configure NSX-T URL Analysis
Objective 2.6 – Describe NSX Segmentation
Objective 2.7 – Describe North-South insertion
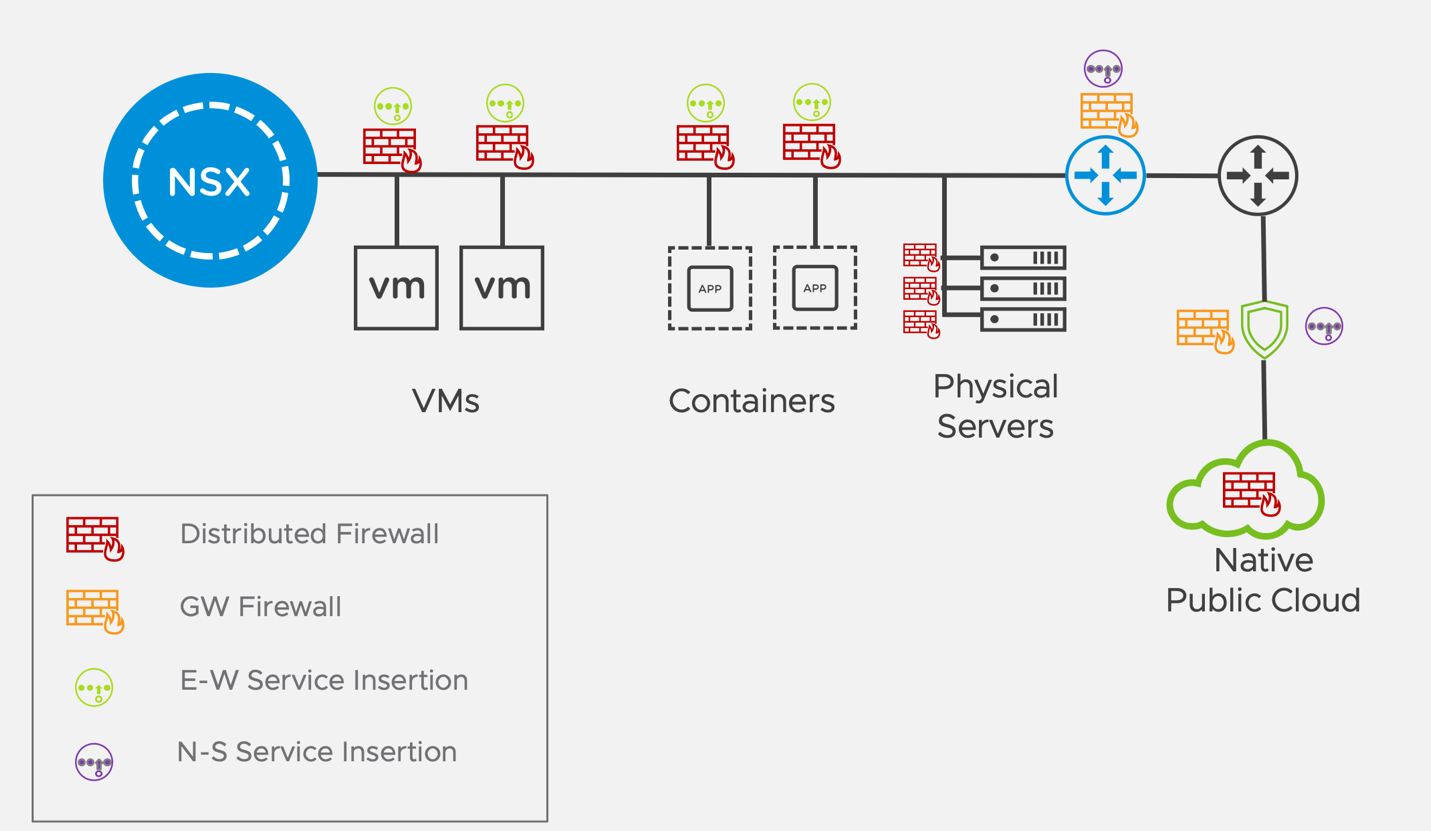
Objective 2.8 – Describe East-West insertion
East West Service Insertion and Service Chaining
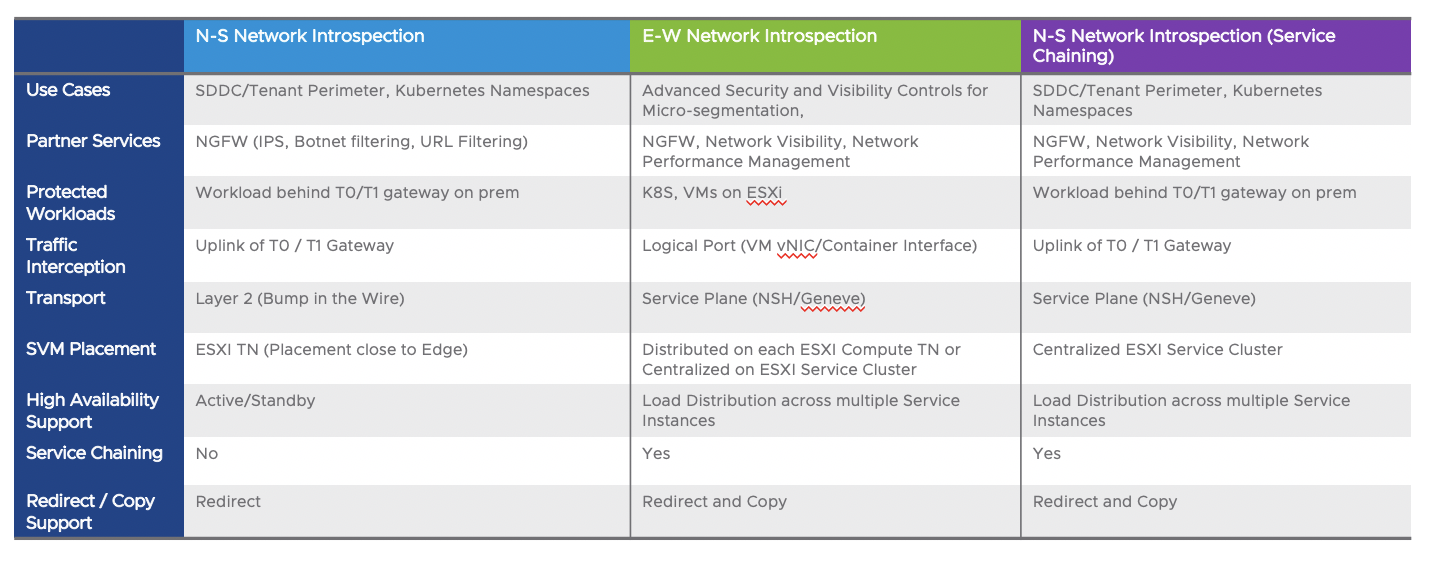
Section 4 – Installing, Configuring, and Setup
Objective 4.1 – Manage users and roles (LDAP, RBAC, Active Directory, etc.)
Access NSX Manager through an Active Directory can be via LDAP and / or vIDM
NSX Data Center Documentation – Integration with LDAP
NSX Data Center Documentation – Role-Based Access Control (RBAC)
NSX Data Center Documentation – Integration with VMware Identity Manager/Workspace ONE Access
NSX Data Center Documentation – Configuring Both vIDM and LDAP or Transitioning from vIDM to LDAP
Objective 4.2 – Configure and manage distributed firewall policies and rules
HOL-2126-01-NET: NSX-T Getting Started
Module 5: DFW and Tools (15 min)
HOL-2126-02-NET -NSX-T – Advanced Security
Module 3: DFW and Tools (15 min)
Objective 4.3 – Configure manage time based firewalls rules
NSX Data Center Documentation – Time-Based Firewall Policy
HOL-2126-02-NET -NSX-T – Advanced Security
Module 3: DFW and Tools (15 min)
Objective 4.4 – Configure identity firewalls rules
NSX Data Center Documentation – Identity Firewall
HOL-2126-02-NET -NSX-T – Advanced Security
Module 6: Identity Based firewall (30 min)
Objective 4.5 – Configure gateway firewalls rules
NSX Data Center Documentation – Gateway Firewall
Objective 4.6 – Configure and manage distributed IDS/IPS (signatures, profiles, rules)
NSX Data Center Documentation – Distributed IDS/IPS Rules
HOL-2126-02-NET -NSX-T – Advanced Security
Module 5: Distributed IDS (45 min)
Objective 4.7 – Configure and manage URL analysis
NSX Data Center Documentation – Context Profiles
HOL-2126-02-NET -NSX-T – Advanced Security
Module 4: NSX-T Context Aware firewall and URL Analysis (30 min)
Objective 4.8 – Install and configure Guest Introspection agent components in VMTools
NSX Security Reference Guide – 7.3 NSX Endpoint Protection – Guest Introspection
Objective 4.9 – Deploy NSX Intelligence appliance
NSX Intelligence Documentation – NSX Intelligence System Requirements
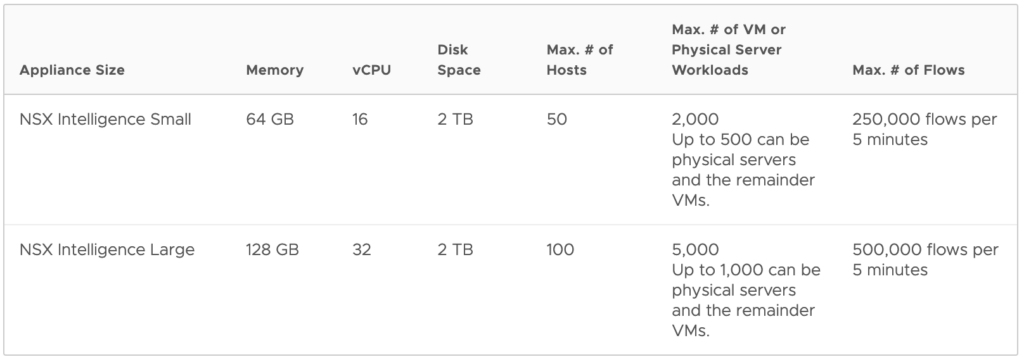
How to deploy NSX Intelligence appliances
NSX Manager System > Configuration > Appliances
- Deploy appliance
- Appliance size
- NSX Intelligence Small VM appliance size is suitable for lab and proof-of-concept deployments, or small-scale production environments
- NSX Intelligence Large VM appliance size is suitable for a production environment
Objective 4.10 – Visualize traffic flows and create security recommendations using NSX Intelligence
VMware YouTube Demo: Distributed Analytics with VMware NSX Intelligence
Tech Field Day YouTube Demo: VMware NSX Intelligence: Policy Creation & Microsegmentation Made Easy
Objective 4.11 – Create and manage security groups
HOL-2126-02-NET -NSX-T – Advanced Security
Module 2: Security Grouping and Policy Concepts (45 min)
Objective 4.12 – Enable logging on hosts and Edge transport nodes
NSX Data Center Documentation – Configure Remote Logging
Section 6 – Troubleshooting and Repairing
Objective 6.1 – Validate guest introspection is operational
NSX Data Center Documentation – Verify Health Status of Service Instance
- The following parameters must be realized in NSX-T Data Center for the health status to change to Up
- Guest virtual machines must be available on the host
- Guest virtual machines must be powered on
- Endpoint protection rules must be applied to the guest virtual machines
- Guest virtual machines must be configured with the supported version of VMtools and file introspection drivers
NSX Data Center Documentation – View Service Deployment Status
View service deployment details on the Monitoring Dashboard.
View the system-wide status of EPP policy.
- Home > Monitoring – Dashboards
- Monitoring – System
- To view the deployment status across clusters in the system, navigate to the Endpoint Protection widget
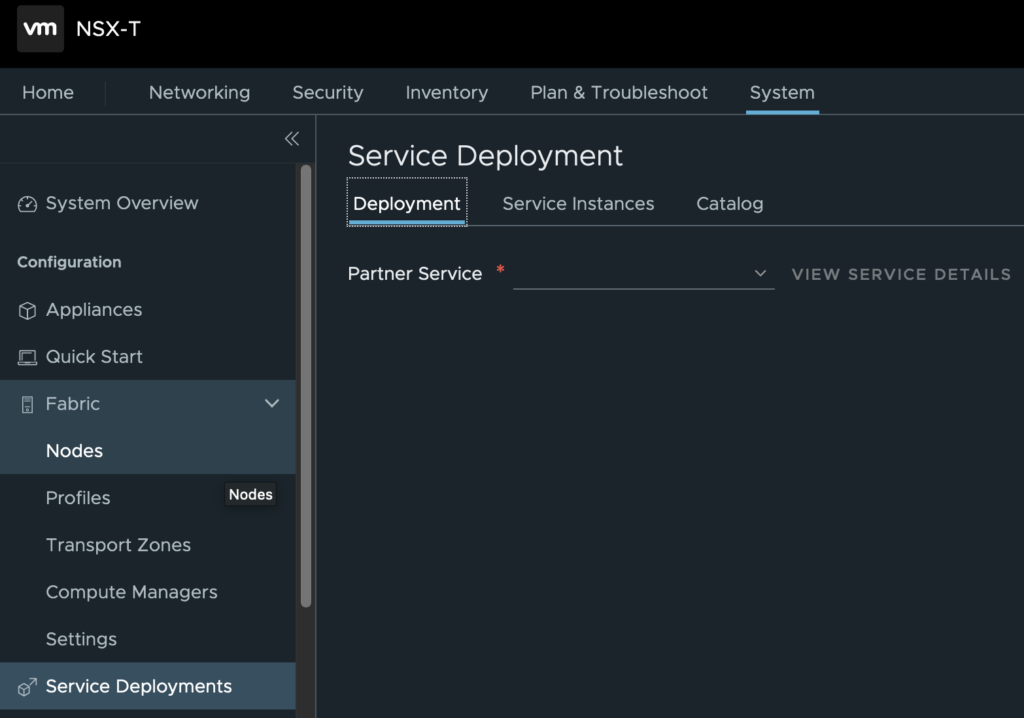
Objective 6.2 – Validate North-South and East-West network introspection is operational
Check the status of the Partner Service in the Service Deployment section
- System > Configuration > Service Deployments
Objective 6.3 – Verify the operation of Distributed Firewall
NSX Data Center Documentation – Check Rule Realization Status
NSX Data Center Documentation – Monitor and Troubleshoot Firewall on NSX Manager
NSX Data Center Documentation – Troubleshooting Distributed Firewall on ESX Hosts
NSX Data Center Documentation – Troubleshooting Distributed Firewall on KVM Hosts
NSX Data Center Documentation – Distributed Firewall Packet Logs
Objective 6.4 – Verify the operation of Gateway Firewall rules
NSX Data Center Documentation – Troubleshooting Gateway Firewall
- Gateway Firewall is enabled for the given Gateway.
- Check the realization state for a given gateway firewall policy. The UI shows the realization status next to the top right side of the FW Policy header.
- Success
- Error
- In Progress
- Unknown
- Check rule stats to see any traffic is hitting the FW policy.
- Enable logging for the rule for troubleshooting the policy.
- On the edge nodes
- Get logical router …
- Get firewall <logical router id> ruleset rules
- Get firewall <logical router id> sync config
- get log-file syslog | find datapathd.firewallpkt
Objective 6.5 – Verify the operation of IDS/IPS
NSX Data Center Documentation – Verify Distributed IDS Status on Host
Objective 6.6 – Verify the operation of URL analysis
NSX Data Center Documentation – URL Analysis Workflow
Objective 6.7 – Identify and review log files and events related to firewalls, IDS/IPS, URL Analysi
NSX Data Center Documentation – Log Messages and Error Codes
NSX Data Center Documentation – Firewall Audit Log Messages
- On NSX-T appliances syslog messages are in /var/log/syslog
- On KVM hosts, syslog messages are in /var/log/vmware/nsx-syslog
- Esx-cli
- get log-file <auth.log | controller | controller-error | http.log | kern.log | manager.log | node-mgmt.log | policy.log | syslog> [follow]
Objective 6.8 – Verify logging is enabled on hosts and Edge transport nodes
NSX Data Center Documentation – Configure Remote Logging
Examples of successful logging in /var/log/syslog
- get logging-servers
- clear logging-servers
- esxcli system syslog config get
- KVM
- /etc/rsyslog.d/00-vmware-remote-logging.conf
Troubleshooting syslog
- Verify the remote log server’s IP address.
- Verify that the levelparameter is configured correctly.
- Verify that the facilityparameter is configured correctly.
- If the protocol is TLS, set the protocol to UDP to see if there is a certificate mismatch.
- If the protocol is TLS, verify that port 6514 is open on both ends.
- Remove the message ID filter and see if logs are received by the server.
- Restart the rsyslogservice with the command
- restart service rsyslogd
To conclude
Hopefully my extensive list of study links and notes in this exam guide helps you preparing for the exam. All the best with your exam.
Cheers, Daniël



2 Comments
sudheer · October 27, 2021 at 1:21 pm
Amazing post very helpful with all the links to read.
Daniël Zuthof · October 27, 2021 at 3:32 pm
Hi Sudheer,
Thanks for your kind words. Happy to hear it’s very helpful to you.
Cheers, Daniël