In this IPv6 series I’d like to tell you about my “journey” to implement the protocol. I already had some knowledge of it, but not extensively. As a first step IPv6 is implemented at home. The plan is to work my way back from home to my lab in the data-center.
The previous parts describe the basics and how to implement IPv6 in my home network using a tunneling technique called 6RD. Using the 6RD tunnel, my ISP assigned a /56 IPv6 prefix, which is awesome. Lots of subnetting possibilities.
The last one talks about obtaining a prefix and thinking through a suitable IP plan. Are you going to use DHCP, SLAAC or both. Finally it gives food for thoughts on dual stack configuration of your routers and essential services like DNS, DHCP, NTP and AAA.
Let’s go to the bits.
The series
My implementation steps will be split into several parts of which this one is the fourth. Other parts in this IPv6 series are:
- Part 1: IPv6 Primer
- Part 2: IPv6 at home using 6RD
- Part 3: Native IPv6 in the Lab
- Part 4: IPSec VPN (this post)
- Part 5: IPv6 with NSX-T
Probable outline of next parts (subject to change)
- Part 6: IPv6 with Cloud Director
Background
From my house to the lab, an IPv4 based IPSec VPN was already configured. The goal is to also be able to route IPv6 traffic to the lab in a secure way. This calls for additional configuration on the Edgerouter 6P at home and on pfSense in the lab.
The config
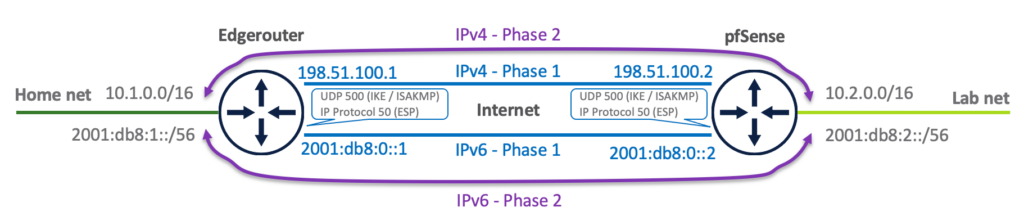
Currently a IPSec – Phase 1 tunnel is configured between the public IPv4 addresses of the Edgerouter and pfSense appliance. A Phase 2 tunnel connects the IPv4 subnets at home and in the lab together. So what would be the next step. Could a second Phase 2 tunnel for IPv6 traffic simply be added to the existing Phase 1, or should a new IPv6 based Phase 1 + 2 be created?
Adding a IPv6 tunnel
It sounds logically to just create an additional IPv6 based Phase 2 to the existing IPv4 based Phase 1, since the IPv6 traffic is tunneled anyway. After trying, it appeared that it depends on the IPSec implementation of the device. pfSense supports adding a IPv6 based Phase 2 to the existing IPv4 based Phase 1.
Mixing IPv4 and IPv6 Phase 2 tunnels within a IPv4 based Phase 1 is not supported on the Edgerouter. The error on the Edgerouter after committing a second Phase 2 tunnel to the config is:
user@edgerouter# commit
[ vpn ]
[ vpn ipsec site-to-site peer 198.51.100.2 tunnel 2 ]
VPN configuration error: IPv6 over IPv4 IPsec is not supported
Commit failed
[edit]
user@edgerouter#Edgerouter configuration
Due to lacking support of mixed tunnels, two Phase 1 tunnels need to be configured. My advise is to configure them using the CLI. Important parameters like IKE version, connection type and local-address are simply not available in the UI. Make sure the remote side is set to respond if the Edgerouter is configured as initiator. The working configuration is:
user@edgerouter# show vpn ipsec
auto-firewall-nat-exclude enable
esp-group FOO0 {
compression disable
lifetime 1800
mode tunnel
pfs dh-group14
proposal 1 {
encryption aes256
hash sha256
}
}
ike-group FOO0 {
key-exchange ikev2
lifetime 3600
proposal 1 {
dh-group 14
encryption aes256
hash sha256
}
}
site-to-site {
peer 198.51.100.2 {
authentication {
mode pre-shared-secret
pre-shared-secret <SomeSecret>
}
connection-type initiate
description "IPSec to Lab"
ike-group FOO0
ikev2-reauth inherit
local-address 198.51.100.1
tunnel 1 {
esp-group FOO0
local {
prefix 10.1.0.0/16
}
remote {
prefix 10.2.0.0/16
}
}
}
#pfSense IPv6 WAN IP
peer 2001:db8:0::2 {
authentication {
mode pre-shared-secret
pre-shared-secret <SomeSecret>
}
connection-type initiate
description "IPSec IPv6 to Lab"
ike-group FOO0
ikev2-reauth inherit
#Edgerouter IPv6 WAN IP
local-address 2001:db8:0::1
tunnel 1 {
esp-group FOO0
local {
prefix 2001:db8:1::/56
}
remote {
prefix 2001:db8:2::/56
}
}
}
}The Firewall
Don’t forget to add additional IPv6 based rules into the firewall alongside the IPv4 rules to allow the needed ports. When possible, do not only allow the required IPSec port and protocol, but also configure the peer IP as source. This prevents all kinds of attacks. At least allow:
- UDP 500 (IKE / ISAKMP)
- IP Protocol 50 (ESP)
On my Edgerouter the WAN6_Local rule looks like:
user@edgerouter# show firewall ipv6-name WAN6_LOCAL
default-action drop
description "WAN6 to Router"
rule 10 {
action accept
description Allow-IPSec-IKE
destination {
address 2001:db8:0::1
port 500
}
source {
address 2001:db8:0::2
}
log disable
protocol udp
}
rule 20 {
action accept
description Allow-IPSec-ESP
destination {
address 2001:db8:0::1
}
source {
address 2001:db8:0::2
}
log disable
protocol 50
}
rule 30 {
action accept
description Allow-ICMP-from-Lab
destination {
address 2001:db8:0::1
}
log disable
protocol icmpv6
source {
address 2001:db8:2::/56
}
}
rule 40 {
action drop
description "Drop invalid state"
state {
invalid enable
}
}As a last step add the “WAN6_Local” rule to your external facing Edgerouter interface to enable IPSec traffic. In my case it’s the 6RD tunnel interface “tun0”.
user@edgerouter# set interfaces tunnel tun0 firewall
in {
ipv6-name WAN6_IN
}
local {
ipv6-name WAN6_LOCAL
}Result
When combining all of the above the result is show in the overview below.
To Conclude
Finally all the (basic) configuration is now done. Using the config in this and previous parts, the goal is reached to have a fully functional IPv6 environment at home and in the lab.
This paves the way to configuring and use IPv6 in NSX-T and subsequently in Cloud Director. Watch out of the next part in the series!
Cheers, Daniël




0 Comments