Today’s NSX-T topic is about automatically configuring hosts with IPv6 addresses. During the writing of my IPv6 series, I wondered what options are available in NSX-T and which use-cases they serve. The full list on IPv6 posts can be found here: IPv6 posts.
In a IPv4 network, DHCP is used widely to automatically configure IP addresses and additional IP stack options like DNS servers / suffix, NTP, PXE or for IP based phones. In the IPv6 world it’s a bit different. Surely DHCPv6 is available, but also Stateless autoconfiguration (SLAAC).
This rises the question which to use (or even both) and in which use case. After reading the documentation and several blog post, I still had question about the Router Advertisement (RA) modes within NSX-T Network Discovery (ND) Profiles and what their role is in IPv6 autoconfiguration..
Last but not least, NSX-T supports the detection of duplicate IPv6 addresses via DAD Profiles and assigning IP addresses via DHCP. Both will be touched later on, but especially since DHCP is a pretty common feature, it will be brief.
ND Profiles
ND Profiles are required when creating a T0 or T1 router. During router creation the profile named “default” is automatically selected, unless configured otherwise. The default ND Profile is configured with RA mode “SLAAC with DNS through RA”, but without DNS parameters. The default ND Profile cannot be modified and therefore a new profile could be needed in certain use-cases. When used, the default profile, effectively enables SLAAC for every segment connected to a T0 or T1 router that has a /64 prefix configured.
If a new ND Profiles is needed, create one by going to “Networking Profiles” > “IPv6” > “Select Profile Type” > “ND Profiles”.
RA modes
During the creation or modification of a ND Profile, the primary parameter is the RA Mode.
Before going into the specifics, it needs mentioning that in the first RA (RFC) specifications, DHCP was required, to configure DNS in combination with SLAAC. Only since the introduction of RFC 8106 (which obsoletes RFC 6106) that became possible. The additional RA parameters for DNS configuration are called RDNSS and DNSSL, which mean:
- RDNSS = Recursive DNS Server
- DNSSL = DNS Search List, a.k.a. DNS domain suffix
Now the foundation is explained, let’s jump to the available RA modes in NSX-T. For readability I’ll explain the modes in the table below, alongside it’s description and use-case(s).
| Mode | Description | Possible use-case |
| Disabled | No automatic IPv6 assignment and no gateway advertisement. | Static IPv6 addressing in native or dual-stacked environments. Parameters configured statically or via DHCPv4. IPv4 only environments if attached segment has no IPv6 prefix configured. |
| SLAAC with DNS through RA (Default) | Stateless IPv6 assignment, gateway advertisement, RDNSS and DNSSL configuration using RA. Only accepts IPv6 DNS server addresses. | Basic IPv6 host configuration using stateless addresses. Usable in Native IPv6 and dual-stacked networks in which address traceability is not required. IPv4 only environments if attached segment has no IPv6 prefix configured. |
| SLAAC with DNS through DHCP | Stateless IPv6 assignment and gateway advertisement using RA. DNS configuration (amongst other possible parameters) using DHCP. | Extended host configuration using stateless addresses. Usable in native IPv6 networks in which address traceability is not required. |
| DHCP with Address and DNS through DHCP | Gateway advertisement using RA. Stateful IPv6 assignment and DNS configuration (amongst other parameters) using DHCP. | Extended host configuration using stateful addresses. Usable in Native IPv6 and dual-stacked networks in which address traceability and extended parameters (DNS, NTP) are required. |
| SLAAC with Address and DNS through DHCP | Stateless IPv6 assignment, gateway advertisement, RDNSS and DNSSL configuration using RA. and Stateful IPv6 assignment and DNS configuration (amongst other parameters) using DHCP. Only accepts IPv6 DNS server addresses. Only supported by NSX Edges, not transport nodes. | Host configuration using stateless and stateful addresses in native IPv6 networks in which address traceability and extended parameters (DNS, NTP) could be implemented depending on host OS compatibility. Used for compatibility reasons in scenarios when different types of host OS’es are used within a segment. The OS’es could have partial or misbehaving IPv6 support and therefore can use all of the options. |
RA mode Operating System support
The right RA mode for your environment could depend on which host OS’es are used and if you’re having control over the used versions. An extended list of Operating Systems and their IPv6 support can be found on Wikipedia.
| OS | IPv6 Support status |
| Android | No support for DHCPv6 |
| iOS / iPadOS | Fully supported |
| Linux | Fully supported |
| macOS | Fully supported |
| Windows Vista, 7, 8, 8.1 | No support for RDNSS and DNSSL via RA |
| Windows 10 up to Anniversary Update (1607) | No support for RDNSS and DNSSL via RA |
| Windows 10 Creators Update (1703) and later | Fully supported |
| Windows Server 2012 (R2), 2016 | No support for RDNSS and DNSSL via RA |
| Windows Server 2019 | Fully supported |
RA Modes in-depth
I you’re interested in low level RA specifics by an NSX-T Edge for each of the RA modes, I’ll show them using Wireshark traces. The settings I used for autoconfiguration are shown below so you can recognize them in the traces.
For SLAAC
- Prefix: 2001:X:X:111::/64
- DNS 1: 2606:4700:4700::1111
- DNS 2:2606:4700:4700::1001
- Suffix: domain.local
For DHCP
- DHCP IP: 2001:X:X:111::e/64
- IP Range: 2001:X:X:111::2-2001:X:X:111::d
- DNS 1: 2001:4860:4860::8888
- DNS 2: 2001:4860:4860::8844
- Suffix: domain2.local
RA Mode: Disabled
This one is simple, no RA frames are send. Windows hosts connected to the segment do ask for them by sending Router Sollicitation frames to the “All-routers” multicast address ff02:2.
RA Mode: SLAAC with DNS through RA
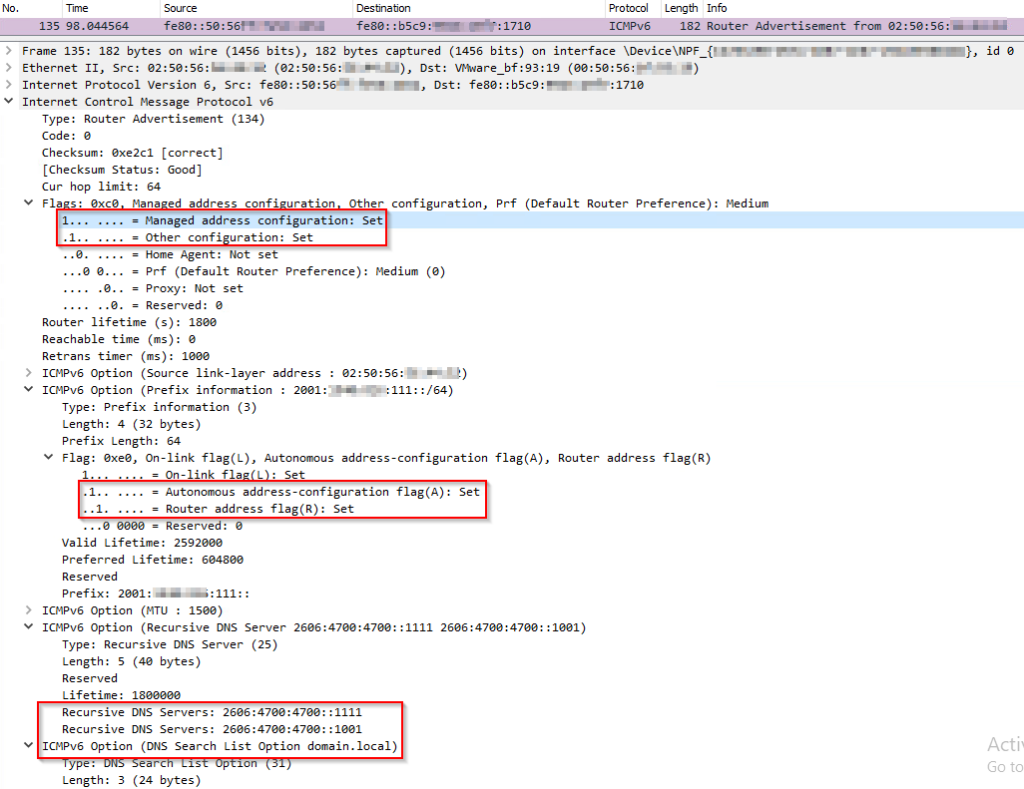
In this mode the NSX-T Edge clearly advertises itself as SLAAC only capable router. That’s because the upper 2 flags (Managed and Other) are both set to “0”. The middle 2 flags (Autonomous and Router) are both set to “1”. On the bottom, the actual DNS options advertised by the router are shown.
RA Mode: SLAAC with DNS through DHCP
In this mode the NSX-T Edge advertises itself as SLAAC capable router that uses DHCP for other options. That’s because “Managed” flag (IP via DHCP) is set to 0 and the “Other” flag (Options via DHCP) is set to “1”. The lower 2 flags (Autonomous and Router) are both set to “1”.
RA Mode: DHCP with Address and DNS through DHCP
In this mode the NSX-T Edge advertises itself as router that uses DHCP for IP address and other options. That’s because “Managed” flag (IP via DHCP) is set to 1 and the “Other” flag (Options via DHCP) is set to “0”. The lower 2 flags that existed before are gone now.
RA Mode: SLAAC with Address and DNS through DHCP
This mode is a bit different. At first the NSX-T Edge advertises itself as regular SLAAC capable router that uses DHCP for Addresses and DHCP for other options. That’s because “Managed” flag (IP via DHCP) is set to 1 and the “Other” flag (Options via DHCP) is set to “1”. Using standard RA frames the Edge sends them to the all-nodes multicast group (ff02::1), so hosts can receive them.
The lower 2 flags (Autonomous and Router) are both set to “1”, which means SLAAC is available. The DNS options which can be seen in the trace for the “SLAAC with DNS through RA” mode, are not available.
Things change a bit when performing a “ipconfig /renew6” on a Windows Server 2019 host connected to the segment. At first the Windows hosts sends a Router Sollicitation (RS) frame to the all-routers multicast group (ff02::2). The result is not what I expected, having first seen the RA frame above.
The result of the RS is a unicast RA frame addressed to the link-local IPv6 address (fe80::/10) of the Windows host. The interesting part is that this frame does has additional DNS related options. See the bottom highlighted part of the RA frame.
The result can be seen in the “ipconfig /all“output below. The connection-specific DNS suffix, primary IP and DNS setting are based on DHCP. It also shows that the SLAAC based DNS setting are applied and added to the list of DNS Servers and search suffix received by DHCP earlier.
DAD Profiles
With IPv6 also comes the capability for detecting and (if possible) prevent duplicate IPv6 addresses. This process is called Duplicate Address Detection (DAD) and is mandatory for all hosts that have IPv6 addresses. DAD is used for all types of IPv6 addresses, including: link-local (fe80::/10), Global Unicast (2000::/3) and Unique Local (fc00::/7) addresses.
DAD can be configured in NSX-T in the form of DAD profiles, which can be found in the same section of the NSX-T UI as ND profiles.
“Networking Profiles” > “IPv6” > “Select Profile Type” > “DAD Profiles”.
The DAD options are very brief. Just two major settings, Loose or Strict mode. The default DAD profile is configured in Loose mode and cannot be modified, but what is the difference?
The documentation is very brief on this topic and does not give a good explanation. Even after looking into RA and Router Sollicatation (RS) frames using Wireshark, I could not find a clue. I’m guessing it’s about DAD “optimistic” mode as described in RFC 4429. I’ll try to find someone in the VMware NSBU team to find out and update this section accordingly.
In general, the intention of DAD “optimistic” mode is to minimize address configuration delays in the successful case, and to reduce disruption as far as possible in the failure case. Optimistic DAD is not intended to improve security, reliability, or robustness of IPv6. The RFC further states that “optimistic” mode should not be used for networks having a large number of static configured hosts, because of the higher probability of duplicate addresses.
It’s important knowing that configuring the DAD profile in either mode, does not impact the DAD configuration on hosts connected to the segment. That’s configured by host OS manufacturer.
DHCP Profiles and configuration
Configuring DHCP in NSX-T is pretty straightforward and has lots of similarities with IPv4. That’s why I choose not to dedicate a detailed section on this topic. DHCP can be configured in either Server of Relay mode. In a dual-stacked environment using DHCPv4 options, using DHCPv6 only for IPv6 addresses could suffice. In an IPv6 only segment, the other parameters like DNS server should also be used together with the suitable RA mode in the ND Profile.
To configure a DHCP Server in NSX-T, the general steps are:
- Create a DHCP Profile in Server mode
- Configure a IP address (if blank, 100.96.0.1/30 is used)
- Bind profile to an Edge Cluster
- Bind the profile to a T1 router (optional)
- Configure DHCP on a Segment
- Configure a DHCP Server IP address
- Configure a IP range
- Configure other DHCP parameters (DNS, NTP, etc.)
That’s basically it for most DHCP implementations. A tip before pulling your hair out if IP addresses are not assigned to your hosts, check if the “Segment Security Profile” is configured accordingly. I’ll touch that in a future NSX-T post.
To conclude
While writing for my main IPv6 series, this topic was at first part of the main story. Initially I thought a single IPv6 part for NSX-T would suffice. In hindsight, there was more to know, just like the NSX-T IPv6 features overview before. For readability I ended up writing a couple of extra (tidbit) posts also.
Digging into this matter was fun and gave a ton of new insights. I guess that why creating content helps for understanding that matter and forces me to write it down in such a way it’s interesting and understandable for you, the reader.
One interesting point to mention is that during the investigation how things work under the hood of an NSX-T Edge, I noticed that an NSX-T Edge uses FRRouting, which I’m guessing is used for many of router related features like: IPv6, BGP, BFD, OSPF and VRF Lite. That’s probably why VMware is listed as a contributor the project.
Useful links
Operating Systems and their IPv6 support















0 Comments