In this IPv6 series I’d like to tell you about my “journey” to implement the protocol. I already had some knowledge of it, but not extensively. As a first step I implemented it at home. The plan is to work my way back from home to my lab in the data-center.
In the previous part of this series, I discussed the IPv6 basics that in my opinion matters the most when starting to implement the protocol. Of course there are dozens of books written about it, but it’s not my intent to go that deep IPv6.
The series
My implementation steps will be split into several parts of which this one is the second. Other parts in this IPv6 series are:
- Part 1: IPv6 Primer
- Part 2: IPv6 at home using 6RD (this post)
- Part 3: Native IPv6 in the Lab
- Part 4: IPSec VPN
- Part 5: IPv6 with NSX-T
Probable outline of next parts (subject to change)
- Part 6: IPv6 with Cloud Director
6RD background
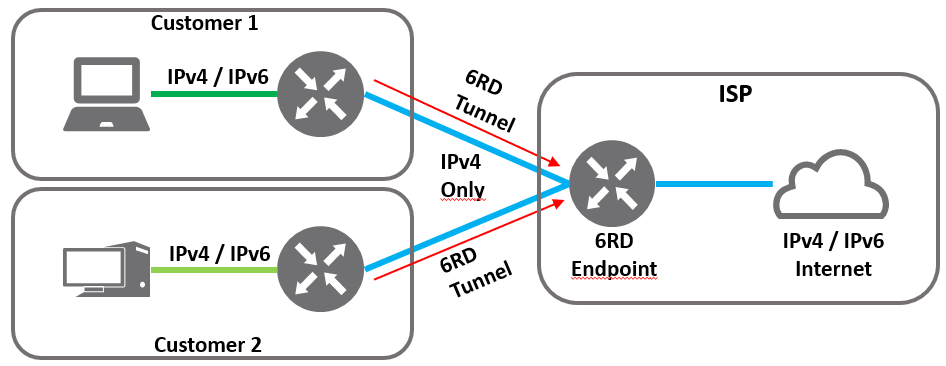
My ISP (Tweak.nl) does not have a native IPv6 implementation available. They do support IPv6 Rapid Deploy or 6RD however, but what is it? In short, 6RD is a protocol that tunnels IPv6 over an IPv4 network to a tunnel endpoint in control of the ISP. 6RD is derived from the 6to4 protocol.
Important to know is that 6RD and 6to4 both use the same encapsulation protocol which is 6in4, but both serve a different purpose. 6RD is developed mainly for consumer ISP’s that want to offer IPv6 services to their customers, but do not offer it end-to-end. The advantages of using 6RD are:
- Implemented entirely within the ISP domain
- Customer can decide to enable IPv6
- Customer has control over 6RD implementation
- No native (end-to-end) IPv6 required
To make use of IPv6 from a customer perspective, the ISP has to provide a 6RD tunnel endpoint (also called relay) which is reachable over IPv4. My ISP has several 6RD tunnel endpoints, depending on the public IPv4 subnet you are assigned to. The drawing below, shows the way it works.
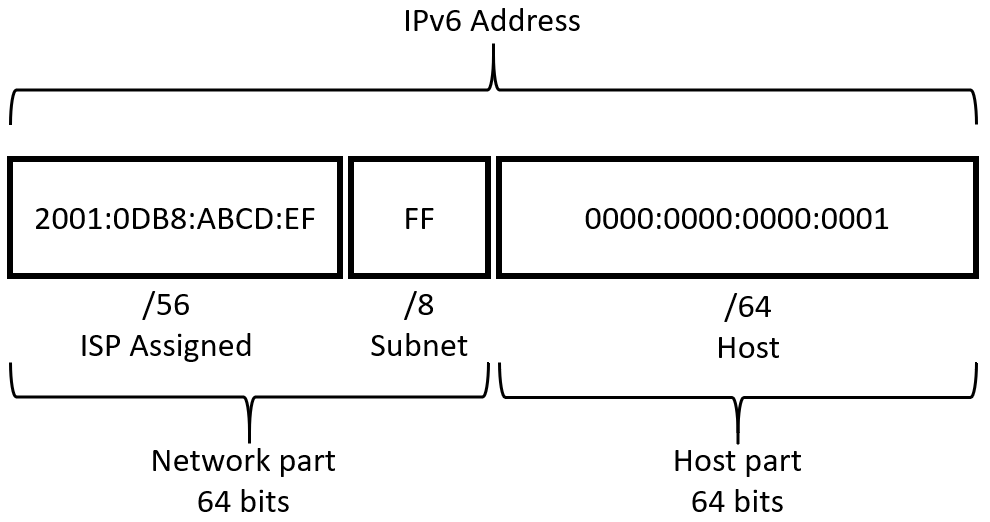
Using 6RD, my ISP provides a /56 IPv6 prefix for the WAN interface of my router. To my internal router interfaces, I assigned a /64 prefix. All of the internal interfaces are configured using SLAAC. This way the devices connected to the router internal interface assign their own IPv6 address within the designated prefix.
Using sub-netting I can split the (ISP assigned) /56 prefix into multiple subnets. Using 8 bits for the subnet, the /56 prefix can be divided into 256 host prefixes of 64 bits each. For consumer purposes, that’s a whole lot of public IP space. Awesome!
One thing to take into account is the 20-byte overhead of 6RD, since IPv6 is tunneled over IPv4 using 6in4. Because of the tunneling overhead, an MTU of 1480 is mostly used on the internal interfaces of the customer router. Because I used SLAAC, the router MTU size is automatically discovered by the hosts on the network.
Current situation
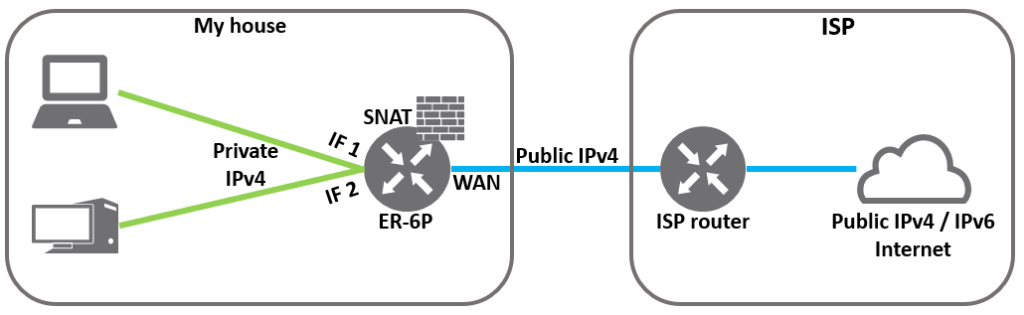
On my home network I use an Ubiquity Edgerouter 6P (with firmware 2.0.9), which supports IPv6 and 6RD. The router is connected to the internet using the ISP assigned static IPv4 address and has no IPv6 configured at all, so pretty standard.
IPv6 prefix calculation
Calculating the 6RD IPv6 prefix, initially was a challenge to me. My ISP did not provide any documentation, so I had to dig around the internet. In hindsight it was quite simple, so let’s do the math.
To calculate the IPv6 prefix for 6RD, you first need to subtract the amount of bits in your ISP provided netmask from /32. This way you calculate the amount of network bits that can be variable for that specific subnet. I know this can be very confusing, so let’s use an example.
On the IPv6 info page of my provided they wrote:
| IP Subnet | IPv6 prefix to use | 6RD relay to use |
| 217.19.16.0/20 | 2a02:58:40::/44 | 217.19.16.18 |
Let’s assume my external (ISP assigned) IP is “217.19.16.128”, which is an IP address within the subnet above. Now subtract the /20 subnet from /32 = /12
Now you are able to calculate your IPv6 prefix based in the info above.
- Go to the site http://silmor.de/ipaddrcalc.html#ip6
- Go to IPv4 to IPv6 Transitional
- Go to the 6to4 and 6RD Network Prefix section
- Fill in Provider prefix IPv6 using the prefix above: 2a02:58:40:: and /44
- Fill in your (examples) external IP: 217.19.16.128 and use 12 bits
- Click ISP -> to Customer
- The field IPv6 Customer prefix now shows the IPv6 prefix you can use. In this example it’s
- 2a02:58:40:8000::/56
If you like a CLI option, ipv6calc can also do the trick.
user@host:~$ ipv6calc --action 6rd_local_prefix --6rd_prefix 2a02:58:40::/44 --6rd_relay_prefix 217.19.16.12/20 217.19.16.128no input type specified, try autodetection…found type: ipv4addr
no output type specified, try autodetection…found type: ipv6addr
2a02:58:40:8000::/56As you can see both results are the same. Let’s configure something!
Configure the EdgeRouter
During my search how to properly configure my EdgeRouter for 6RD, the post of fellow tweaker “Dubbeldrank” on the Tweakers.net forum, together with the post of Jedadiah Casey with his blog post IPv6 6RD with Ubiquiti and DD-WRT helped me out. Thanks and credits to both.
Configure 6RD tunnel
I’m assuming you already have a working IPv4 configuration and IP protocol 41 (6in4) is allowed for outgoing connections in your existing IPv4 firewalls outgoing rulese, because 6in4 is the actual tunneling protocol used by 6RD.
First we’ll need to configure a new tunnel interface with sit (6RD) encapsulation. Open an SSH session to your EdgeRouter and configure the bits.
set interfaces tunnel tun0 address '2a02:58:40:8000::1/56'
< I used the first IP in the prefix ::1 >
set interfaces tunnel tun0 description 'IPv6 6RD Tunnel'
set interfaces tunnel tun0 encapsulation sit
set interfaces tunnel tun0 local-ip 217.19.16.128
< Use your external IP >
set interfaces tunnel tun0 multicast disable
set interfaces tunnel tun0 remote-ip 217.19.16.18
< Use the ISP provided 6RD relay host >
set interfaces tunnel tun0 ttl 255
set protocols static interface-route6 '::/0' next-hop-interface tun0
commit
saveNow you should be able to reach IPv6 hosts on the internet from the EdgeRouter. Use ping6 to test.
user@er-6p# ping6 google.nl -c 1
PING google.nl(ams16s32-in-x03.1e100.net (2a00:1450:400e:80c::2003)) 56 data bytes
64 bytes from ams16s32-in-x03.1e100.net (2a00:1450:400e:80c::2003): icmp_seq=1 ttl=121 time=6.74 msFirewall
Let’s create some rules to protect the devices on your internal network. This step is important since your devices will get public IPv6 addresses, once the EdgeRouters internal interfaces are configured for IPv6.
WAN to LAN
set firewall ipv6-name WAN6_to_LAN6 default-action drop
set firewall ipv6-name WAN6_to_LAN6 description 'Internet6 to LAN6'
set firewall ipv6-name WAN6_to_LAN6 rule 10 action accept
set firewall ipv6-name WAN6_to_LAN6 rule 10 description 'Allow Incoming IPv6 established or related connections'
set firewall ipv6-name WAN6_to_LAN6 rule 10 state established enable
set firewall ipv6-name WAN6_to_LAN6 rule 10 state related enable
set firewall ipv6-name WAN6_to_LAN6 rule 20 action drop
set firewall ipv6-name WAN6_to_LAN6 rule 20 state invalid enable
set interfaces tunnel tun0 firewall in ipv6-name WAN6_to_LAN6
commit
saveLAN to WAN
set firewall ipv6-name LAN6_to_WAN6 default-action accept
set firewall ipv6-name LAN6_to_WAN6 description 'LAN6 to Internet6'
set firewall ipv6-name LAN6_to_WAN6 rule 10 action accept
set firewall ipv6-name LAN6_to_WAN6 rule 10 state established enable
set firewall ipv6-name LAN6_to_WAN6 rule 10 state related enable
set firewall ipv6-name LAN6_to_WAN6 rule 20 action drop
set firewall ipv6-name LAN6_to_WAN6 rule 20 state invalid enable
set firewall ipv6-name LAN6_to_WAN6 rule 30 action accept
set firewall ipv6-name LAN6_to_WAN6 rule 30 description "Allow ICMPv6 packets"
set firewall ipv6-name LAN6_to_WAN6 rule 30 protocol icmpv6Interface configuration
Now the tunnel interface and firewall rules are created, both internal router interfaces can be configured for IPv6. As mentioned in the “Prefix calculation” section, I’m going to use a /64 for every interface. The /64 is derived from the ISP assigned /56. In this example I use 2 prefixes for eth1 and eth2
- 2a02:58:40:8000::1/56 is used for eth0 (external)
- 2a02:58:40:8001::1/64 is used for eth1 (internal 1)
- 2a02:58:40:8002::1/64 is used for eth2 (internal 2)
Before IPv6 was added, the router already was acting as IPv4 based DHCP server for all my devices to serve basic parameters like DNS Servers, DNS suffix. There parameters stay the same, since name resolving an IPv6 AAAA record can be resolved just fine from the IPv4 stack. Check out the “Current situation” section for more info.
In the new situation, I’m going to use SLAAC for stateless IPv6 host auto-configuration. The config includes also the IPv6 MTU size, hop-limit and Router Advertisement. IPv6 will be configured on both of my internal networks with it’s own IPv6 prefix of which hosts can derive their IPv6 addresses.
Interface 1
This section configures the first internal interface on the EdgeRouter.
If you’re using a EdgeRouter-X or similar Marvell based router swap “ethernet eth1” with “switch switch0”.
set interfaces ethernet eth1 address '2a02:58:40:8001::1/64'
< 01 (the 8 bits after the ISP assigned /56) is used for the subnet >
< The first IP in the prefix ::1 is used for the router interface >
< An /64 prefix is used for the hosts part >
set interfaces ethernet eth1 ipv6 dup-addr-detect-transmits 1
set interfaces ethernet eth1 ipv6 router-advert cur-hop-limit 64
set interfaces ethernet eth1 ipv6 router-advert link-mtu 1480
set interfaces ethernet eth1 ipv6 router-advert managed-flag false
set interfaces ethernet eth1 ipv6 router-advert max-interval 300
set interfaces ethernet eth1 ipv6 router-advert other-config-flag false
set interfaces ethernet eth1 ipv6 router-advert prefix '2a02:58:40:8001::1/64' autonomous-flag true
set interfaces ethernet eth1 ipv6 router-advert prefix '2a02:58:40:8001::1/64' on-link-flag true
set interfaces ethernet eth1 ipv6 router-advert prefix '2a02:58:40:8001::1/64' valid-lifetime 2592000
set interfaces ethernet eth1 ipv6 router-advert reachable-time 0
set interfaces ethernet eth1 ipv6 router-advert retrans-timer 0
set interfaces ethernet eth1 ipv6 router-advert send-advert true
< Attach the IPv6 firewall ruleset to the interface >
set interfaces ethernet eth1 firewall in ipv6-name LAN6_to_WAN6Interface 2
This section configures the second internal interface on the EdgeRouter.
set interfaces ethernet eth2 address '2a02:58:40:8002::1/64'
< 02 (the 8 bits after the ISP assigned /56) is used for the subnet >
< The first IP in the prefix ::1 is used for the router interface >
< An /64 prefix is used for the host part >
set interfaces ethernet eth2 ipv6 dup-addr-detect-transmits 1
set interfaces ethernet eth2 ipv6 router-advert cur-hop-limit 64
set interfaces ethernet eth2 ipv6 router-advert link-mtu 1480
set interfaces ethernet eth2 ipv6 router-advert managed-flag false
set interfaces ethernet eth2 ipv6 router-advert max-interval 300
set interfaces ethernet eth2 ipv6 router-advert other-config-flag false
set interfaces ethernet eth2 ipv6 router-advert prefix '2a02:58:40:8002::1/64' autonomous-flag true
set interfaces ethernet eth2 ipv6 router-advert prefix '2a02:58:40:8002::1/64' on-link-flag true
set interfaces ethernet eth2 ipv6 router-advert prefix '2a02:58:40:8002::1/64' valid-lifetime 2592000
set interfaces ethernet eth2 ipv6 router-advert reachable-time 0
set interfaces ethernet eth2 ipv6 router-advert retrans-timer 0
set interfaces ethernet eth2 ipv6 router-advert send-advert true
< Attach the IPv6 firewall ruleset to the interface >
set interfaces ethernet eth2 firewall in ipv6-name LAN6_to_WAN6Host config
My home network worked just fine with IPv4 only. All IP basic parameters were already assigned by the DHCP server running on my EdgeRouter.
With the addition of IPv6 (using SLAAC) on the EdgeRouters internal interfaces, everything continued to work just fine. Only the IP addresses on all of my devices had to be renewed, before they could communicate using IPv6.
Let’s check the IP addresses bound to my workstation after renewing them.
PS C:\Users\user> ipconfig /renew6 LAN
Windows IP Configuration
Ethernet adapter Ethernet 3:
Connection-specific DNS Suffix . : lh.loc
IPv6 Address. . . . . . . . . . . : 2a02:58:40:8002:2016:7e1f:fc3c:8ec0
Temporary IPv6 Address. . . . . . : 2a02:58:40:8002:c520:8382:23c9:4eef
Link-local IPv6 Address . . . . . : fe80::2016:7e1f:abcd:efc0%6
IPv4 Address. . . . . . . . . . . : 192.168.x.x
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::7683:c2ff:abcd:efa8%6
192.168.x.xNow this host has an public IPv6 address, how cool is that!
Checking IPv6 connectivity
Now my host has an public IPv6 address, it’s time for some tests to make sure everything works fine.
Connectivity test
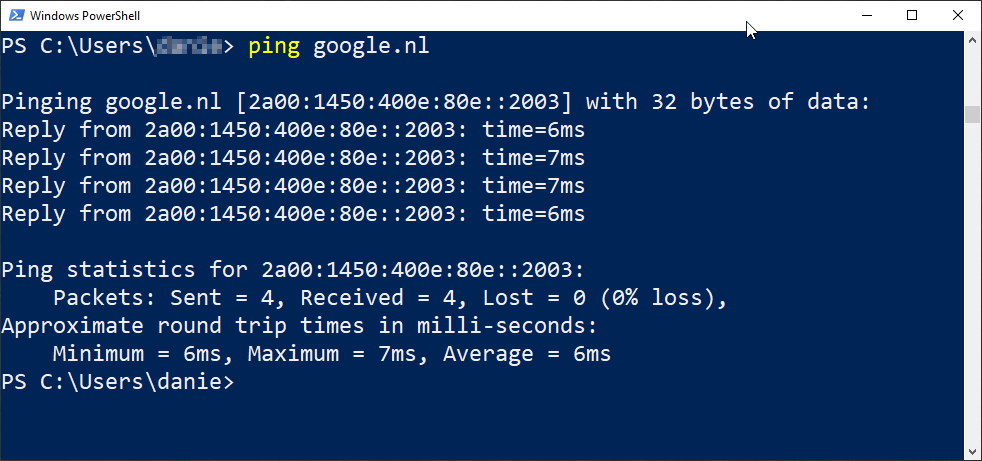
First a basic IPv6 ping will suffice.
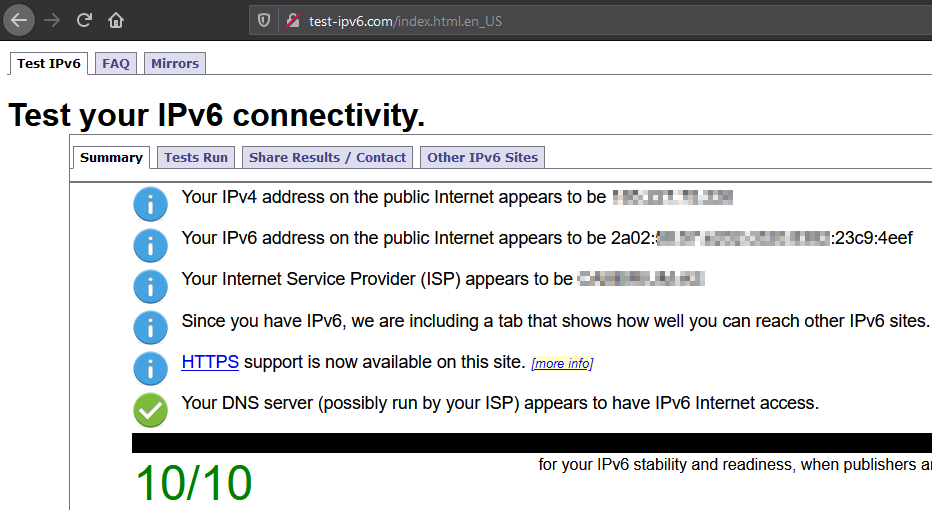
After the ping test, check your general IPv6 connectivity with Test your IPv6. (test-ipv6.com).
Also check if packets using various MTU sizes work fine. Test-ipv6.com has a test for that.
When the test above give the expected result, you’re good to go with IPv6. Let’s go on in the next section, to check if the firewall on your EdgeRouter is properly configured.
Firewall test
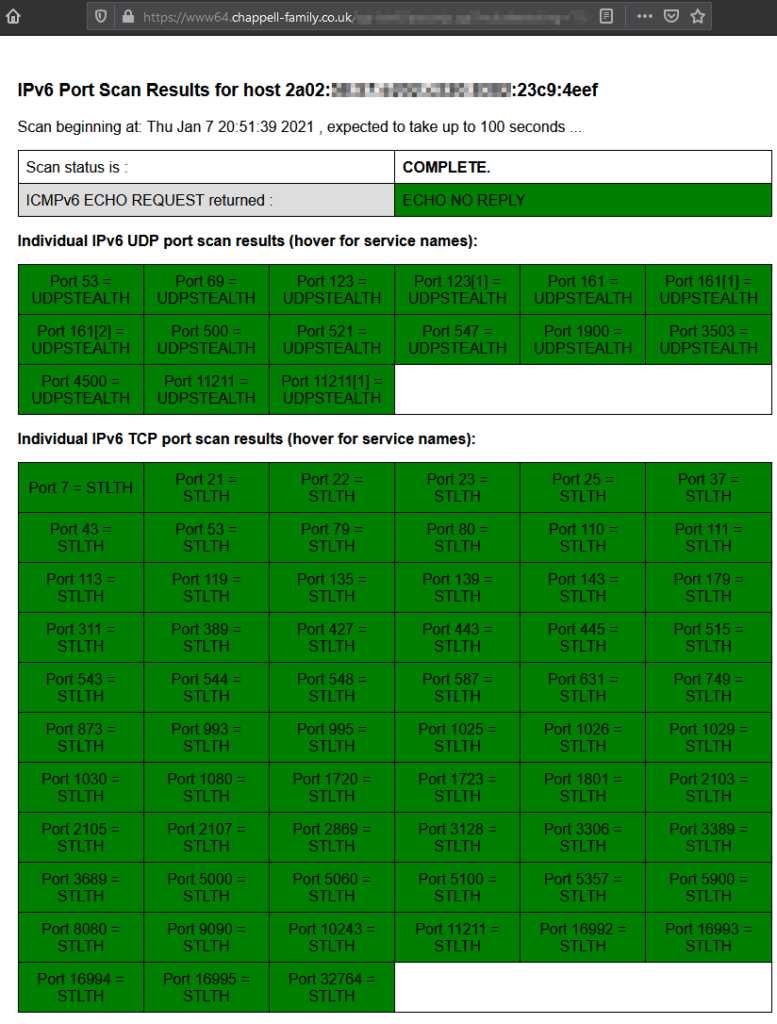
As mentioned earlier, IPv6 uses public addresses within your internal network. Because of it, you’re not automatically “protected” by the IPv4 NAT Masquerading . Let’s find out by using an online IPv6 Port Scanner if the firewall is configured okay.
All fine! The firewall on the EdgeRouter is configured correctly to use IPv6 in a safe way.
Other options to get IPv6
If your ISP does not support IPv6 natively of via 6RD, but you want try it out, there are other options. Hurricane Electric (HE) has a free 6in4 Tunnel Broker service available that provides you with a /48 prefix.
Important to mention is that when using this service, all your IPv6 traffic will route through the HE network and probably the latency will be increased. Check out their terms of service first.
If your want to use the Tunnel Broker service, use the post by Nish Vamadevan to configure it on an EdgeRouter.
Other devices
Maybe you’re more into MikroTik routers and their RouterOS. In that case check out the post of Olaf van Zandwijk to configure IPv6 6RD on such a device.
To conclude
The intent of this post is to ease the configuration IPv6 in your home network. If your ISP has native IPv6, use that. If not, the 6RD option is a good replacement if they provide that service. Else you could always go ahead with the Tunnel Broker service.
With that said, I must say configuring and using IPv6 was interesting to do, gave additional insights in the matter and last but not least, it was fun to learn something new.
Cheers, Daniël
Useful links
Wikipedia
General
IPv6 Connectivity tests
IPv6 Port Scanner / Firewall Tester
Community blogs
Tweakers.net Forum – Ubiquity devices (Dutch)
IPv6 6RD with Ubiquiti and DD-WRT



0 Comments